Crack Htpasswd John The Ripper Linux
- Crack Htpasswd John The Ripper Linux Command
- Crack Htpasswd John The Ripper Linux Iso
- Crack Htpasswd John The Ripper Linux Download
- Crack Linux Password Hash John The Ripper
Security of your important data is the most crucial concern, John the Ripper is a free tool widely used by ethical hackers and security testers to check and crack passwords. It lets you identify weak passwords and take measures to harden your security. Due to the popularity of this tool, it is part of security focused Linux distributions like Kali Linux. Crack Facebook Password With John The Ripper blltly.com/1lmjh7. Cracking an Ubuntu password with John the Ripper is very easy. All that is needed is a good wordlist and the John The Ripper utility. Install the John the Ripper password cracking utility. Learn how to crack /etc/shadow file using John the Ripper. Thu 09 Jan 2020 /Hacking/Cracking; In this article we are going to show how we can crack /etc/shadow file using John the Ripper. It is common in CTF like events to somehow get access to the shadow file or part of it and having to crack it so you can get the password of a user.
Password cracking is a mechanism that is used in most of the parts of hacking. Exploitation uses it to exploit the applications by cracking their administrator or other account passwords, Information Gathering uses it when we have to get the social media or other accounts of the C.E.O. or other employees of the target organization, Wifi Hacking uses it when we have to crack the hash from the captured wifi password hash file, etc.
So to be a good Ethical hacker one must be aware of password cracking techniques. Though it is easy to crack passwords by just using guessing techniques, it is very time consuming and less efficient so in order to automate the task, we have a lot of tools. When it comes to tools Kali Linux is the Operating System that stands first, So here we have a list of tools in Kali Linux that may be used for Password Cracking.
1. Crunch
In order to hack a password, we have to try a lot of passwords to get the right one. When an attacker uses thousands or millions of words or character combinations to crack a password there is no surety that any one of those millions of combinations will work or not. This collection of a different combination of characters is called a wordlist. And in order to crack a password or a hash, we need to have a good wordlist which could break the password. So to do so we have a tool in Kali Linux called crunch.
crunch is a wordlist generating tool that comes pre-installed with Kali Linux. It is used to generate custom keywords based on wordlists. It generates a wordlist with permutation and combination. We could use some specific patterns and symbols to generate a wordlist.
To use crunch, enter the following command in the terminal.
2. RainbowCrack
Rainbow crack is a tool that uses the time-memory trade-off technique in order to crack hashes of passwords. It uses rainbow tables in order to crack hashes of passwords. It doesn’t use the traditional brute force method for cracking passwords. It generates all the possible plaintexts and computes the hashes respectively. After that, it matches hash with the hashes of all the words in a wordlist. And when it finds the matching hashes, it results in the cracked password.
To use RainbowCrack, enter the following comamnd in the terminal.
3. Burp Suite
Burp Suite is one of the most popular web application security testing software. It is used as a proxy, so all the requests from the browser with the proxy pass through it. And as the request passes through the burp suite, it allows us to make changes to those requests as per our need which is good for testing vulnerabilities like XSS or SQLi or even any vulnerability related to the web. Kali Linux comes with burp suite community edition which is free but there is a paid edition of this tool known as burp suite professional which has a lot many functions as compared to burp suite community edition. It comes with an intruder tool that automates the process of password cracking through wordlists.
To use burp suite:
- Read this to learn how to setup burp suite.
- Open terminal and type “burpsuite” there.
- Go to the Proxy tab and turn the interceptor switch to on.
- Now visit any URL and it could be seen that the request is captured.
4. Maltego
Maltego is a platform developed to convey and put forward a clear picture of the environment that an organization owns and operates. Maltego offers a unique perspective to both network and resource-based entities which is the aggregation of information delivered all over the internet – whether it’s the current configuration of a router poised on the edge of our network or any other information, Maltego can locate, aggregate and visualize this information. It offers the user with unprecedented information which is leverage and power.
Maltego’s Uses:
- It is used to exhibit the complexity and severity of single points of failure as well as trust relationships that exist currently within the scope of the infrastructure.
- It is used in the collection of information on all security-related work. It will save time and will allow us to work more accurately and in a smarter way.
- It aids us in thinking process by visually demonstrating interconnected links between searched items.
- It provides a much more powerful search, giving smarter results.
- It helps to discover “hidden” information.

To use Maltego: Go to applications menu and then select “maltego” tool to execute it.
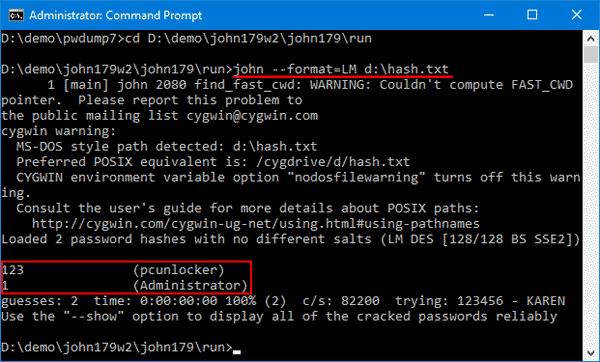
5. John the Ripper
John the Ripper is a great tool for cracking passwords using some famous brute for attacks like dictionary attack or custom wordlist attack etc. It is even used to crack the hashes or passwords for the zipped or compressed files and even locked files as well. It has many available options to crack hashes or passwords.
To use John the Ripper
- John the ripper comes pre-installed in Kali Linux.
- Just type “john” in the terminal to use the tool.
Recommended Posts:
Crack Htpasswd John The Ripper Linux Command
If you like GeeksforGeeks and would like to contribute, you can also write an article using contribute.geeksforgeeks.org or mail your article to contribute@geeksforgeeks.org. See your article appearing on the GeeksforGeeks main page and help other Geeks.
Please Improve this article if you find anything incorrect by clicking on the 'Improve Article' button below.
John is different from tools like HDRA. Hydra makes a blind brute force attack by trying the user name / password combination on the FTP server or telnet server’s service backend. However, John needs hashing first. So, the bigger challenge for hackers is to get the hash that needs to be cracked first. Today, it’s easier to crack hashes with the free rainbow table available online. Just go to one of the sites and submit the hash; if the hash consists of a common word, the site will display that word almost immediately. Rainbow table basically stores common words and corresponding hashes in a huge database. The larger the database, the more words it contains.
But if you want to crack passwords locally on your system, John is one of the great tools worth trying. John is one of the top 10 security tools in Kali Linux. On Ubuntu, it can be installed through the Synaptic Package Manager.
In this article, I will show you how to use the unshadow command together with John to crack a user’s password on a Linux system. On Linux, the user name / key details are stored in the following two files.
The code is as follows:
/etc/shadow

The actual password hash is stored in / etc / shadow; you can access the file as long as you have root access to the machine. So try to access the file from your own Linux system. Or create a new user with a simple password first. I’ll create a new user on my Linux system called happy with the password chess.
The code is as follows:
Adding user `happy’ …
Adding new group `happy’ (1001) …
Adding new user `happy’ (1000) with group `happy’ …
Creating home directory `/home/happy’ …
Copying files from `/etc/skel’ …
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
Changing the user information for happy
Enter the new value, or press ENTER for the default
Full Name []:
Room Number []:
Work Phone []:
Home Phone []:
Other []:
Is the information correct? [Y/n] y
[email protected]:~#
For the sake of demonstration, it’s better to use a simple password, so you don’t have to wait too long. Since our new user has been created, we can now crack their password.
The unshadow command will basically combine the data of / etc / passwd and / etc / shadow to create a file with user name and password details. The usage is quite simple.
The code is as follows:
Usage: unshadow PASSWORD-FILE SHADOW-FILE
[email protected]:~# unshadow /etc/passwd /etc/shadow > ~/file_to_crack
We redirect the output of the unshadow command to a file named file_ To_ New file for crack.
step
Now let’s take a look at the specific steps. After cracking the password successfully, the jhon.pot Password only:
1. Enter the / root / john-1.7.8/run directory and read / etc / shadow with the tool unshadow provided by Jhon
The code is as follows:
Eg: for root users, you can cat / etc / shadow > / root / john-1.7.8/run/ passwd.txt
The first step is to use single crack mode to crack
Crack Htpasswd John The Ripper Linux Iso
The code is as follows:
Specifically for people who use accounts as passwords, they will try a variant of the user name john.conf Medium[ List.Rules Rules defined in: single]
The code is as follows:
If the crack is successful, you can view it jhon.pot Or use:
The code is as follows:
3. The second step is to use wordlist mode to crack
Wordlist mode is a relatively simple mode, as long as you determine where the dictionary file is jhon.conf There is a default dictionary file ‘wordlist = $John’ in the configuration file/ password.lst ’In the run directory password.lst File, wordlist Mode rule in jhon.conf Medium[ List.Rules : wordlist] module definition in[ List.Rules There’s another one under wordlist[ List.Rules The: NT] module is a variant rule that defines rules.
The code is as follows:

Or
The code is as follows:
The fourth step is to use incremental mode to crack
Incremental is the most powerful mode. It will enumerate all combinations and crack them as passwords. It is very time-consuming. There are [in] in the configuration file cremental:All ],[In cremental:Alpha ],[In cremental:Digits ],[In cremental:Alnum ],[In cremental:LanMan ]And so on. Each module name has a corresponding date file under run.
The code is as follows:
Crack Htpasswd John The Ripper Linux Download
Crack Linux Password Hash John The Ripper
5. The fifth step is to use external mode to crack
External allows users to write their own cracking mode of C language jhon.conf We already have some crack mode programs.
Parameter interpretation
–Stdout outputs the results to the screen
–Restore continues to execute from the place where the last decryption was interrupted. If the execution is interrupted by Ctrl + C, the current status will be stored in a document named restore. Use — restore to read the location of the last interrupt from restore, and then continue to crack
–Session sets the name of the current log file
–Make charset character frequency table, which can be used in incremental mode
–Show shows that the password has been cracked because john.POT No account information is stored. When using show, you should input the relevant passwd file
–Test to test the cracking speed of various types of passwords executed by the machine
–Users can only crack the password of an account, which can be the user name or uid number. Adding ‘-‘ before it means not cracking the password of the relevant user
–Groups only crack the password of users in a group. Adding ‘-‘ before it means not cracking the password of users in a group
–For users who use a certain type of shell, the prefix ‘-‘ means no cracking
–Salt can only crack the password whose salt is greater than count. Salt is the basic unit used by UNIX as password coding
–Predefined password cracking types DES / bsdi / MD5 / BF / AFS / LM/